In the January/February issue of last year, WHN introduced readers to the DoD’s new cybersecurity protocol that it will require of all prime and subcontractors. In the article, we interviewed Nicholas McBride, Cybersecurity Consultant at Ecuron, who took us through the steps for compliance. Nicholas recently contacted us to provide important updates for the CMMC Protocols.
There is a link to the original article at the end of this article for full review. Basically, the Office of the Under Secretary of Defense for Acquisition and Sustainment, in conjunction with DoD stakeholders, have developed the new CMMC Certification as a means to protect sensitive information from a range of cyber threats. The intent is to combat the loss of intellectual property and certain unclassified information from the DoD supply chain.
This past November, the DOD put out a rule saying they were changing the CMMC program. It has taken a few months for the changes to obtain a level of clarity, and Nicolas outlined the major changes for us. The previous version was version 1.2, and the new version is 2.0. “The two big takeaways were that they got rid of all of the requirements that went above and beyond the NISTSP 800–171 controls. So that means there were an additional 20 controls for CMMC at Level III. They removed those and it is now just the same 110 controls from the NIST standard,” Nicholas detailed. He also mentioned they got rid of the additional maturity requirements but warned that even though they are not explicitly mentioned, they are implicitly required.
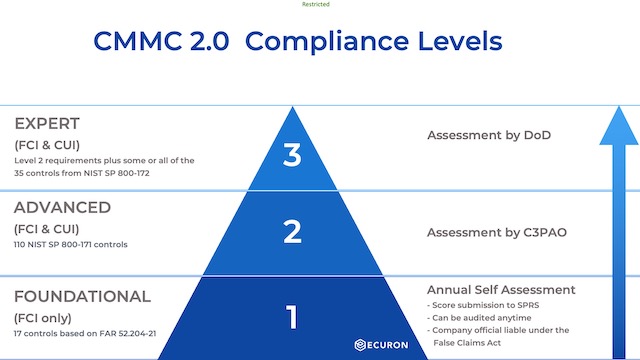
The next big difference is the streamlining of the security levels. The old CMMC model had five levels, with most people aiming for Level I or Level III (Level II having been an intermediary step, and not really a compliance level). The new version only has three levels (fig. 1). Level I has not changed. The new Level II is the same as the old Level III (eliminating the intermediary step), and the new Level III is the same as the old Level V, (eliminating the old Level IV intermediary step). It is still expected that most companies will need Level I or Level II certification, with only a small subset requiring the new Level III.
“The next thing they changed is the rollout,” Nicholas advised. “The previous CMMC Version 1.2 had a phased rollout up through 2025, releasing more contracts every year, starting with 15 last year, all the way up to several hundred by 2025.” Instead, they announced, somewhat ambiguously, there will be a cutover date, likely within the next 9 to 24 months. “There have been updates since then in which they have stated they are looking to get that date would be May of 2023,” he clarified.
The DoD also stated that CMMC Certification may not be necessary for every single contract following May 2023. “They are still slightly unclear on whether it will be every contract, or just a majority of contracts. But my personal speculation is that most people will need to think about it because, if nothing else, the prime contractors are going to be asking for those certifications for their own vendor risk management programs.”
Under the CMMC Framework, the DoD will certify third party assessment organizations who will be able to certify companies to CMMC. Nicholas disclosed that, to date, no companies have been authorized by the DoD to audit companies for certification. “There are still a few minor details they are trying to hammer out, and current speculation puts it around August 2022. Hopefully by then, the 3rd party companies will start performing certification assessments. One thing we do know for sure is there are currently 213 companies who are 3rd party candidates, but they still have to go through their own CMMC assessment from the federal government.” Asked why the holdup on accreditation of the 3rd party companies, Nicholas said the DoD wouldn’t be specific, but indicated the auditing companies were having difficulty developing documentation for the maturity levels.
Current Prime Contractor Requirements
Even though there is ambiguity on the part of the government on dates of implementation and the number of contracts affected, the basic framework is in place and all subcontractors should be well on the path to certification by now. More importantly, he advised that most prime contractors are taking steps to make sure their subcontractors are implementing the framework. “Over the past year, prime contractors have been sending out self-assessment questionnaires (SPRS) to their subcontractors asking if they have assessed their cybersecurity practices against the NIST SP 800-171 guidelines. The next thing they will often ask is if companies have implemented multi-factor authentication and encryption and whether or not the encryption is up to a Federal Information Processing Standards (FIPS) validated standard. This is because the DOD is highly concerned about multi-factor authentication and FIPS validated encryption is now the mandatory standard.”
Nicholas mention the prime contractors are also asking if their subcontractors have adhered to the basic cyber security protocols has put forth by FAR 52.204-21, and whether or not they are planning on becoming CMMC registered, and what the timeline for that is.
Nicolas summed up the current situation with CMMC. “It’s still coming. They’ve tightened up their timeline and made it slightly less complicated, but they are still being just as strict about ensuring that people meet the requirements. We fully expect this to be in place by May 2023.”
About Ecuron
Ecuron is a boutique cybersecurity consulting company that specializes in preparing companies to face cyber threats. Their mission is to create a partnership with you, securing your data and protecting your organization every step of the way. For help developing and implementing an information and cybersecurity strategy for your organization and for more information visit https://www.ecuron.com
You can contact Nicholas at [email protected] or at (713) 646-5044.
Follow this link to the original WHN article https://bit.ly/3md1pnu